13. Will passkeys be a bed of roses?
Surely being promoted by Google, Microsoft, and Apple, passkeys must be the next big thing!
Intro
Passkeys, announced by Apple, Google, Microsoft, and the FIDO Alliance in May 2022, are a replacement for passwords. In this newsletter I will:
show where passkeys fit
describe why we need passkeys
present a passkey primer because how they actually work is quite important
list some key problems with passkeys
suggest that passkeys are far from a complete solution and not THE answer.
Where do passkeys fit?
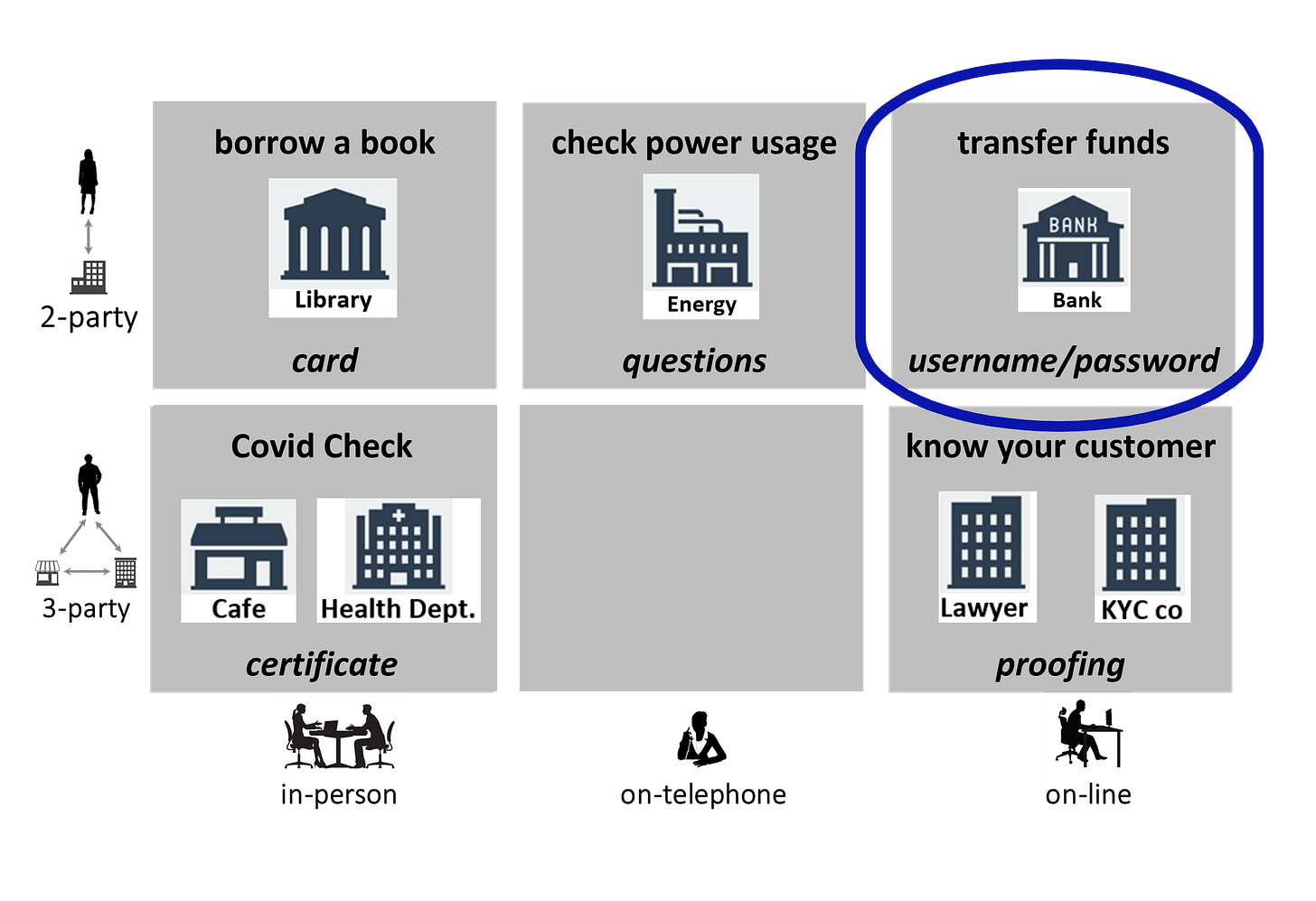
Passkeys replace passwords. They are a unique cryptographic key for each website or app that a person signs onto. Like passwords, passkeys are a form of authentication. Remember this diagram (from my newsletter 2):
So, passkeys are not a full identity solution, but they perform a fundamental function within Identity, this being authentication.
And passkeys fit in a niche - they are not the saviour for all identity scenarios:
Passkeys work on-line for established relationships (2-party transactions). That is, they work when you are signing on to an existing account you opened sometime before, for example a bank account. They do not have any relevance for in-person or on-telephone situations, and they do not have any relevance when establishing relationships (3-party transactions) such as Know Your Customer, when you are opening an account. For a full explanation of this framework, see my newsletter 3 and my newsletter 4.
So passkeys are limited in function (authentication) and in scope (on-line accounts already opened).
Why do we need passkeys?
Secure on-line access is a real problem now, so passkeys are very relevant, even if they do not solve every problem we have. The culprit is a particular type of phishing — on-line username and password phishing. That is, you are tricked onto a site and give away your username and password. This is a problem and it is why so many sites now have moved to multi-factor authentication (MFA). But even with MFA, phishing is still possible, even if it is less prevalent.
The Fast ID Online Alliance (FIDO) has a solution they call 2FA for second factor authentication. FIDO 2FA is provided by a hardware device called a FIDO security key that often looks like a USB flash drive. These devices use public key cryptography to provide very high levels of security. But they are costly and they are painful to replace, and so they have not taken off.
We need something better, so FIDO, Google, Apple, and Microsoft invented passkeys that go beyond FIDO 2FA.
A passkey primer
So how do they do it? I’ll discuss both the functionality, and how that functionality is implemented.
Passkey Functionality
The three principal processes involving passkeys are:
setting up a passkey
signing on using a passkey
administering of passkeys
1. Setting up
You start by signing off the old way. Then, somewhere in the app or website, you select an option to set up a passkey. You are asked if you want to save a passkey for the site:
You confirm saving the passkey by entering your Windows Hello PIN (this is your PC PIN - the one you might use when you boot your PC) and Windows confirms the passkey is saved.
2. Signing on
This is part of a signon page presented by a Chrome browser running on a Windows 11 PC. You don’t enter anything, you simply click in the signon username box.
The first thing to notice is that passkeys work a bit like a password manager! You click in the signon username box and the browser gives you passkey options (if they have been setup), in the same way as a password manager gives you username / password options. There is nothing to remember!
So you activate a signon field in the website, confirm the use of the passkey, and you are in. Well almost – there is a second step:
In this scenario, the passkey is secured by Windows Hello which validates the use of the passkey, in this case through the entry of a PIN (there are alternative ways: face and fingerprint).
And note that a passkey functions very much like a password manager with MFA, in that both require an initial selection followed by a second factor of authentication.
An advantage of passkeys is that the two steps are local to one device, in this case a PC. There is no need for a separate smartphone to confirm the signon.
3. Passkey administration
On a Windows 11 PC there are three places for passkey administration:
the application itself
the Google Password manager
Windows 11 settings
The applications I have seen list the passkeys and allow them to be deleted. The Google password manager simply defaults through to Windows 11 Settings below:
Passkeys are embedded in the Operating System (OS)
In these examples, the passkey is saved within Windows 11, the Microsoft OS and the passkey is tied to a device. Yes, that is important!
So, while passkeys function in a similar manner to password managers for the user (i.e. they make the process somewhat automated), the implementation is totally different (i.e. cloud for password manager, local OS for passkeys). This has implications as described below.
And the problems
My analysis of passkeys above, and my reading, suggest that passkeys are user friendly and totally secure against phishing. That is, you cannot phish a passkey. Great - one big tick there. So what’s the problem?
Passkeys don’t stop phishing attacks!
Hold on, didn’t I just say they cannot be phished? Well, passkeys work in the sense that they are unphishable. But phishing sites can still phish for usernames and passwords. Passkeys do not stop bad people sending fake emails in order to steer users into fake websites that then steal usernames and passwords.
So what can they do with a stolen username / password?
Well, use them! Yes, the bad people can simply go to any PC not set up with a passkey for that website, and they will be prompted for username / password, and then perhaps some form of MFA. And, as we know, they can then break me!
The benefits of internet openness are eroded
Remember that the internet and browsers give us openness and access from any point. If the problem above is solved by making passkeys obligatory (which is very difficult because you need to signon to set up a passkey), then you will be tied to specific devices for those services. So, if the service is a bank, you will not be able to check your balance from work or a friend’s PC – you will have to use your own devices with passkeys already setup.
Passkeys are dangerous if you share devices!
Whoa, surely passkeys don’t make things dangerous! Well, we are not sure yet, but they do open up some theoretical holes. For example, say a company has a loan PC and everyone knows the Microsoft Hello PIN. If a person saves a passkey on that PC, against the advice of the service provider, then it is seemingly useable by anyone who uses that PC.
Put another way, the Microsoft user becomes the actual user. If you know the PC’s PIN you have access to all passkeys and Microsoft provides a list of them all for you (see passkey administration above). That is a bit interesting to say the least.
Giving control to Google, Microsoft, and Apple
Like so many things in IT, the politics of control are rarely broached. The FIDO Alliance has many members including the big five IT companies and many of the major identity companies. FIDO has been promoting 2FA FIDO security keys since 2013.
Passkeys looks like a second attempt to solve the phishing problem, but are based upon using hardware in PCs and smartphones. This has appeal in finding a hardware-based solution without requiring a new piece of hardware.
But, and this is a very big but, while conceptually elegant, practically this puts the OS providers, Google, Microsoft, and Apple, smack in between users and their service providers. Your access to services is through your OS identity and your OS identity is controlled by your OS provider. I wonder if they will start charging for this service one day? Maybe this is why they are cooperating at the moment?
Note that even though Apple’s passkey implementation will be different, they too will be in a controlling position.
Passkeys are not the answer
Passkeys are not a bed of roses! And passkeys are not the answer to Identity.
No doubt they are developing and will develop further, but in this early stage:
passkeys only do authentication for on-line 2-party transactions
passkeys are an un-phishable authentication method that does not stop phishing
passkeys may limit the openness of the Internet
passkeys create a problem with shared devices
passkeys, if successful, put Google, Microsoft, and Apple even more in control than they are now
One has to ask, “Is this the best we can do?” Passkeys look like a half-baked concept designed by a committee. Passkeys look like an attempt to rectify a previous failure, and are more like a bed of thorns than a bed of roses.














Then again .. over at MacRumors
https://www.macrumors.com/2024/10/15/fido-alliance-portable-passkeys-across-platforms/
> Passkeys are also resistant to online attacks like phishing, making them more secure than things like SMS one-time codes.
… say what now?
David Heinemeier Hanson ( https://www.linkedin.com/in/david-heinemeier-hansson-374b18221 ) agrees with you …
https://world.hey.com/dhh/passwords-have-problems-but-passkeys-have-more-95285df9