18. Is the EU Digital Identity Wallet Doomed?
Big projects often result in big failures...
There is a lot at stake for the European Union (EU) Digital Identity Wallet (EUDIW) initiative. It is the biggest identity initiative on the planet.
While it has great aspirations, I think it is doomed from the start, as it fails to consider the small issue of implementation on the ¾ billion current EU smartphones.
The Initiative
The EUDIW, created through legislation, will be the central technology for EU Digital Identity! This is the big play for the 2020s.
The EUDIW is driven by EU eIDAS regulation. eIDAS, or “electronic identification and trust services”, regulates electronic transactions. The initial 2014 regulation known as eIDAS 1.0 was revised to become eIDAS 2.0 in May 2024.
EIDAS 2.0 essentially legislates the EUDIW into existence and the EUDIW is central to EU Digital Identity.
This is no ordinary wallet: it is the fundamental technology for Identity for decades to come.
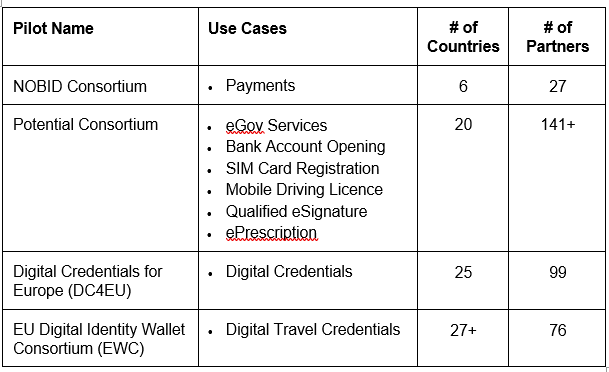
The Pilots
To support this, the EU is financing four pilots to the tune of 40-50 million euro. The pilots consider different use cases:
Two things stand out:
a focus on user functionality – the structure is clearly the use of identity as opposed to the underlying practicality of implementing identity.
a cast of thousands – 100s of large organizations, both governmental and commercial, and literally thousands of people involved. This is no ‘skunk works’ driving to a rapid solution; this is an EU megaproject.
Making the EUDIW Secure
Now, just to be clear, the EUDIW is the central technology that holds all Personal Identity Information (PII). The EUDIW is a decentralized approach in which the wallet holder goes from EU country to EU country freely sharing their PII as they see fit.
So the EUDIW needs to be secure.
The small issue of making the EUDIW secure is described in the Architecture and Reference Framework 1.4. Section 4.3 Architecture Types states that:
“…at least four different types of architecture for the EUDI Wallet Solution can be identified, each leveraging a different type of Wallet Secure Cryptographic Device (WSCD):
Remote Wallet Secure Cryptographic Device (Remote WSCD): In this architecture, the Wallet Secure Cryptographic Device is situated remotely, separate from the user's device, for example - implemented by the Wallet Provider using an HSM.
Local External Wallet Secure Cryptographic Device (Local External WSCD): If a device lacks sufficiently secure hardware, such as a secure element, external hardware components like smartcards may be necessary to enhance security. This architecture involves an external Wallet Secure Cryptographic Device that is connected to, or interacts with, the User's device, to provide cryptographic functions, for example - a hardware token or smart card.
Local Wallet Secure Cryptographic Device (Local WSCD): This architecture refers to a scenario where the Wallet Secure Cryptographic Device is integrated directly within the User's device. This includes solutions like eSIM/eUICC and eSE. In these scenarios, the WSCA (e.g., a Java Card applet) might be deployed by the Wallet Provider. Other examples are based on native solutions, such as StrongBox (Google) and SecureEnclave (Apple), in which access to the WSCD is facilitated via the operating system of the User device.
Hybrid architecture: This architecture combines two or more of the previous three approaches.”
The Implementation Problem
Now here is the problem – if the EUDIW is going to be useful, it needs to work for people and those people in the EU have roughly ¾ billion smartphones. Remember, we cannot leave anyone out. So how will these solutions fit the current ¾ billion smartphones:
Do the security centrally – well, it might work but why bother? If the whole solution revolves around central security infrastructure why not use a central infrastructure for the whole solution? Why would anyone come up with such a complex solution when a simpler solution is available?
External device – you must be joking. We will get a device that can integrate with ¾ billion smartphones. Plug and play for 750,000,000 different brands, models, OS versions etc! Not this decade and unlikely to be in the next either!
Use the security of the smartphone. I’ve seen that tried and failed when simply using one brand of smartphone. Trying to get uniformity of smartphone OSes is the stuff of science fiction and trying to retrofit 750,000,000 smartphones not possible.
Any two of three – even harder!
The EUDIW Project will fail to reach its goals
The EUDIW project is playing in the fun end of Digital Identity, imagining all the neat and wonderful use cases that can please everyone. Fancy that – some bureaucrats coming up with some good PR!
The actual challenging aspect is making it work for a large installed base of smartphones and that is inherently difficult. The implementation challenge is not being faced and the EU has, as yet, no answer.
And, I maintain, it has no answer because there is no answer! It is inherently problematic to secure PII on personal digital devices.
The partial rescue options
If the EUDIW fails to deliver in full, I see two possibilities:
the EU gives it all to Apple and Google
the EU simply declares EUDIW a success based on lesser functionality
Now Apple and Google already own a lot of us, so they would no doubt be keen to own all of us. Passing Digital Identity to them would simply formalize the relationship by passing over the keys. No need for governments to worry about the future of identity! Of course, this would be calamitous and must be avoided. If Self-sovereignty was the goal, we do not want to fall back to no sovereignty at all.
The second option is more likely. A lesser EUDIW functionality will be a signed document on a smartphone. For example a mobile drivers license (mDL). Such technology has benefits as the license can be certified as being authentic but it is also limited, just like physical document, as it does not identify and authenticate the person. It is simply a copy of a credential.
But a document on a smartphone is not a Digital Identity solution!
This will be interesting viewing!
All the best for New Year
Regards
Alan