16. Will decentralized identity work?
Will decentralized identity really work? Everything is opinion at present as there are many open questions.
There is an interesting ‘decentralized identity conversation’ starting here on Substack and if you are just catching up - here’s where we are:
Phil Windley wrote Decentralized Identity Comes of Age
I responded with Yeah, yeah, yeah, yeah, yeah, nah, in which I asked:
Is there someone who can distil all that amazing work into a decentralization design we can all understand?
And Phil obligingly answered in his post What Is Decentralized Identity?
I learnt a lot about decentralization through this last post, but I still had one of those nagging doubts about the efficacy of the solution. As I reflected on Phil’s post I recognized that the “will it work?” question needs to cover more than design. Specifically we need:
design (a given requirement for any new solution) - a topography of people and technology, including interactions and information.
security (fundamental to the identity challenge) - how confidential data is secured, and why the solution is secure.
implementation (difficult for any solution that aims to become a standard) - how the solution can be implemented for large user populations.
So here is my take on the challenges for decentralization in these important areas.
Design
In Phil’s response, the decentralized design still includes Decentralized Identifiers (DIDs), but two additional elements, digital wallets and verifiable credentials, have been identified as ‘needed’.
These additions show that decentralized identity is an evolving discipline and so there is much to ask, including two fundamental design challenges:
The First Design Challenge - doing the hard bit first!
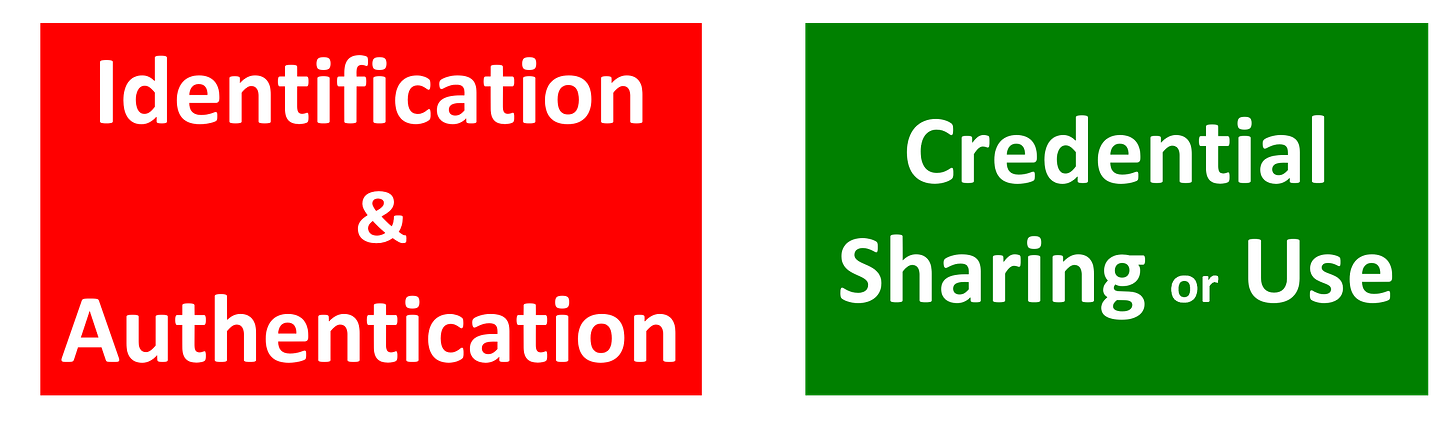
I’ll use my model of the identity process to illustrate this:
This model shows that identification and authentication, i.e. saying who you are and proving that you are who you say you are, precede utilizing credentials for some purpose. No identity solution can be complete without both these components.
Phil’s explanation shows a digital wallet and describes how autonomous software components could potentially interact and exchange credentials securely. But we still do not know how access to the wallet is controlled. If this is not ‘the’ big identity issue of how the actual person is identified and authenticated, then what is?
Yes, the credential use is there, but surely an identity solution needs to be more than that? If access to the digital wallet is predicated on the security of the smartphone, doesn’t that make the solution simply a distributed credential solution, which raises the obvious question of “why bother?”
The Second Design Challenge - a macro hybrid solution?
At the macro level, Phil’s design shows a decentralized identity utilizing other identity solutions to load their own structures with credentials. If this is the case, the macro view of multiple complementary identity solutions should be made explicit and the design rationale for such a hybrid solution justified.
A hybrid solution may ‘work’ but is that what we really need or want?
Security
This is clearly fundamental to an identity solution. Decentralization based on a digital wallet with autonomic identifiers (local storage, if I have read it correctly) requires both an app and local data to be secured. How is this achieved? Does it rely on the security provided by the relevant smartphone operating system, does it utilize the hardware cryptographic capabilities of the smartphone, or is there some other bespoke approach to security?
This is important, and remember that much of decentralization is predicated on the lack of trust for major corporations that leak identity data all too often. Surely decentralization should not be just another leaky solution?
Is there a relatively simple explanation of how security is achieved by decentralization?
Implementation
If you want to try something really hard, try implementing a complex software solution on every smartphone in a country. That is, within reason, support every model sold in the last decade and still being used. That is every operating system version and every variant of crypto support hardware.
For an app that is simply a front for cloud-based data, implementation over multiple smartphone variants is relatively simple as the app is simply a presentation layer. For a decentralized digital wallet, the challenge of implementing complex infrastructure for a population is extreme.
How will decentralization achieve this?
Summary
The current status of the decentralization model appears to remain somewhat conceptual rather than contextual. That is, the concept is a good idea and easy to buy into, but the contextual challenge of making it work is being left to the developers!
This status is confirmed by the lack of working prototypes. And if decentralization were more fully developed, we should expect to see such prototypes and we don’t!
So, for me, “Will it work?” remains an open question, and yeah, yeah, yeah, yeah, yeah, nah is still a distinct possibility.
As you have read this newsletter, and perhaps others, it would be great to get your thoughts. Please comment, below, or write your own post and link back - whatever works for you.
Until the next time ...
Regards
Alan